AI needs your data
Claude Code and Cowork are most powerful when they can query your databases directly. But giving AI raw database access is a risk you can't afford.
Secure database access for AI
Connect your databases to Claude Code, Cowork, and other AI coding tools — with policies, audit logs, and full control over every query.
Works with
The question is how safely they get it.
Claude Code and Cowork are most powerful when they can query your databases directly. But giving AI raw database access is a risk you can't afford.
When an AI coding tool runs a query, who triggered it? What data came back? Without logging, every AI-generated query is a blind spot.
Hand-rolling database permissions for every AI tool burns engineering time. You need managed database access that works out of the box.
See it in action
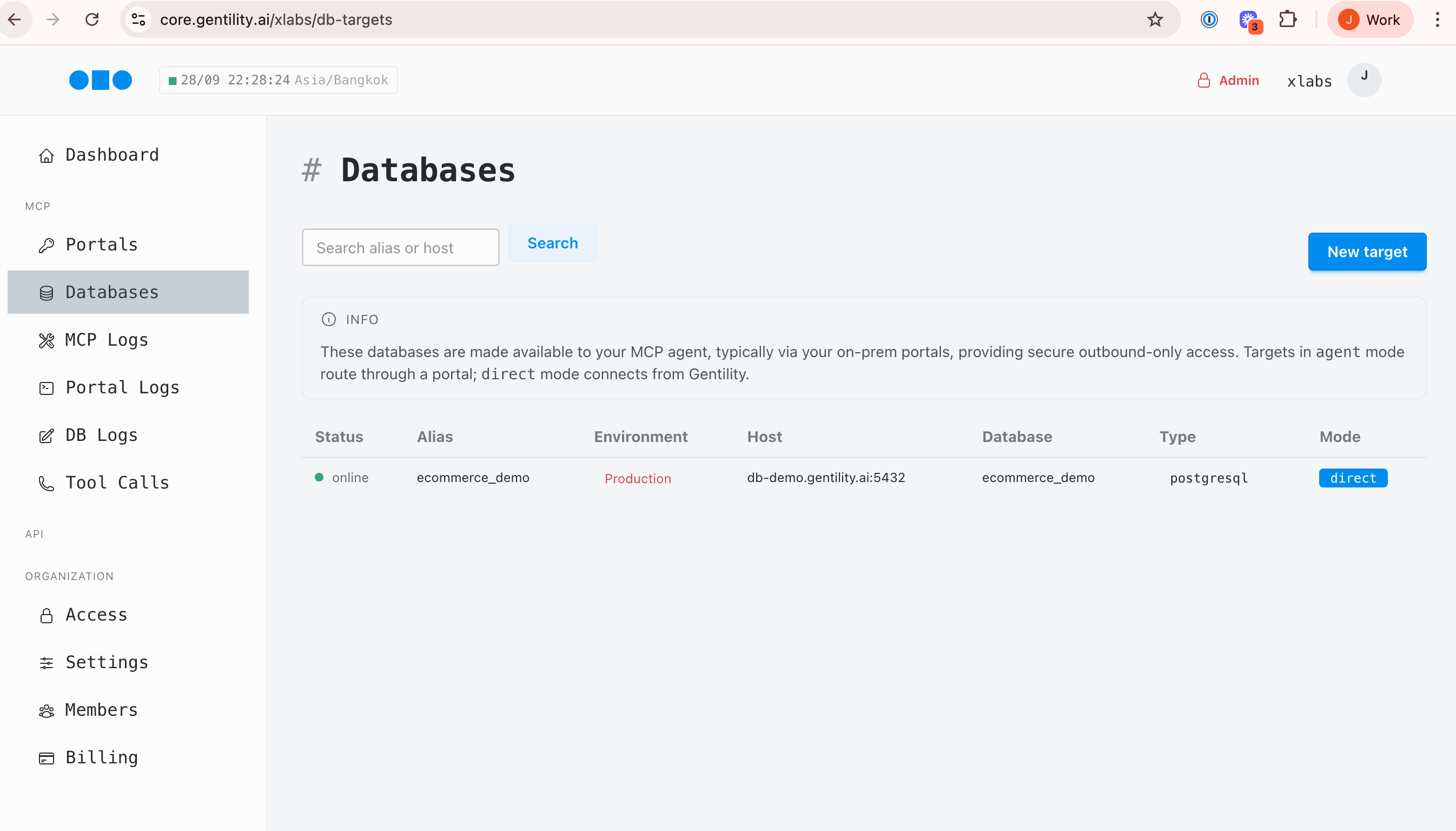
Add PostgreSQL, MySQL, or any database. The agent runs in your infrastructure — your credentials never leave your network.
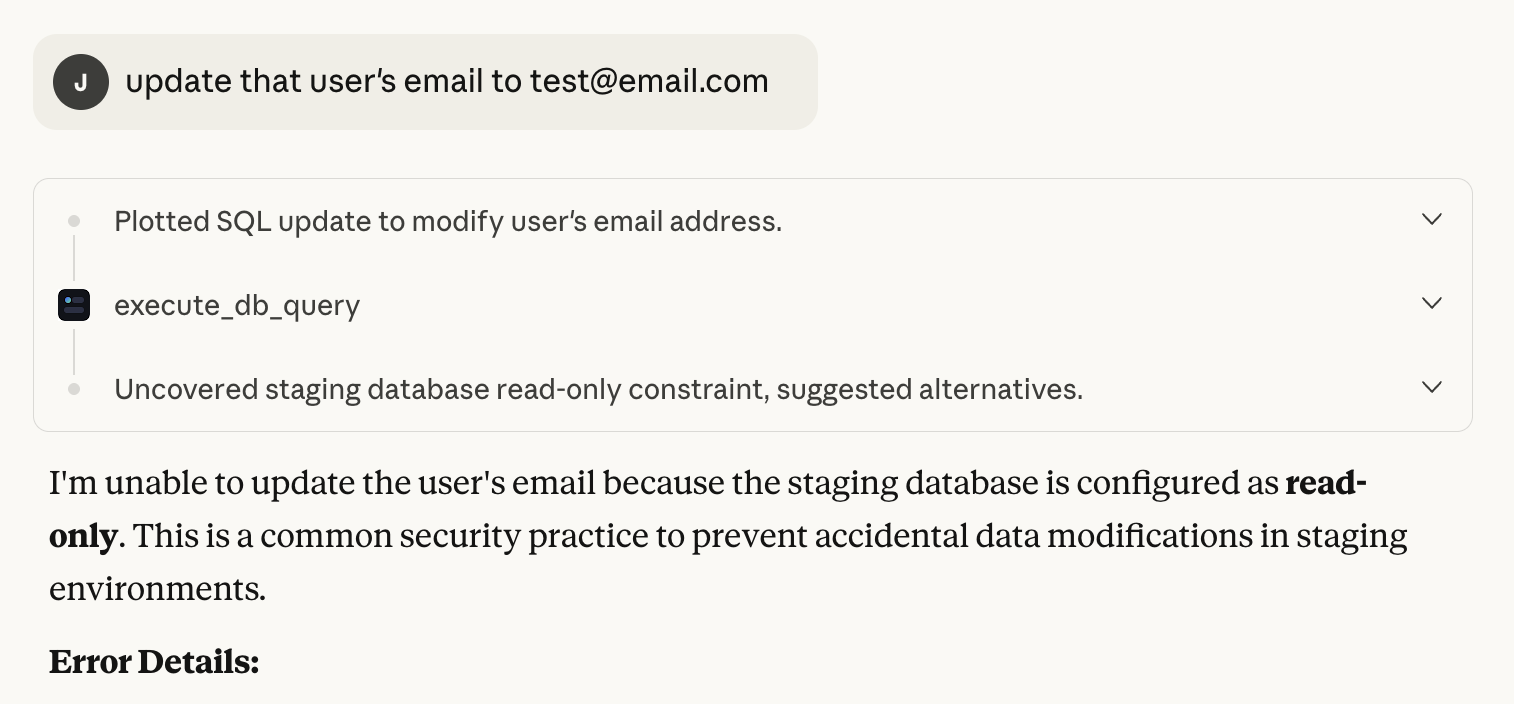
Set read-only defaults, allow-list queries, block dangerous patterns. Policies are enforced on every query, in real time.
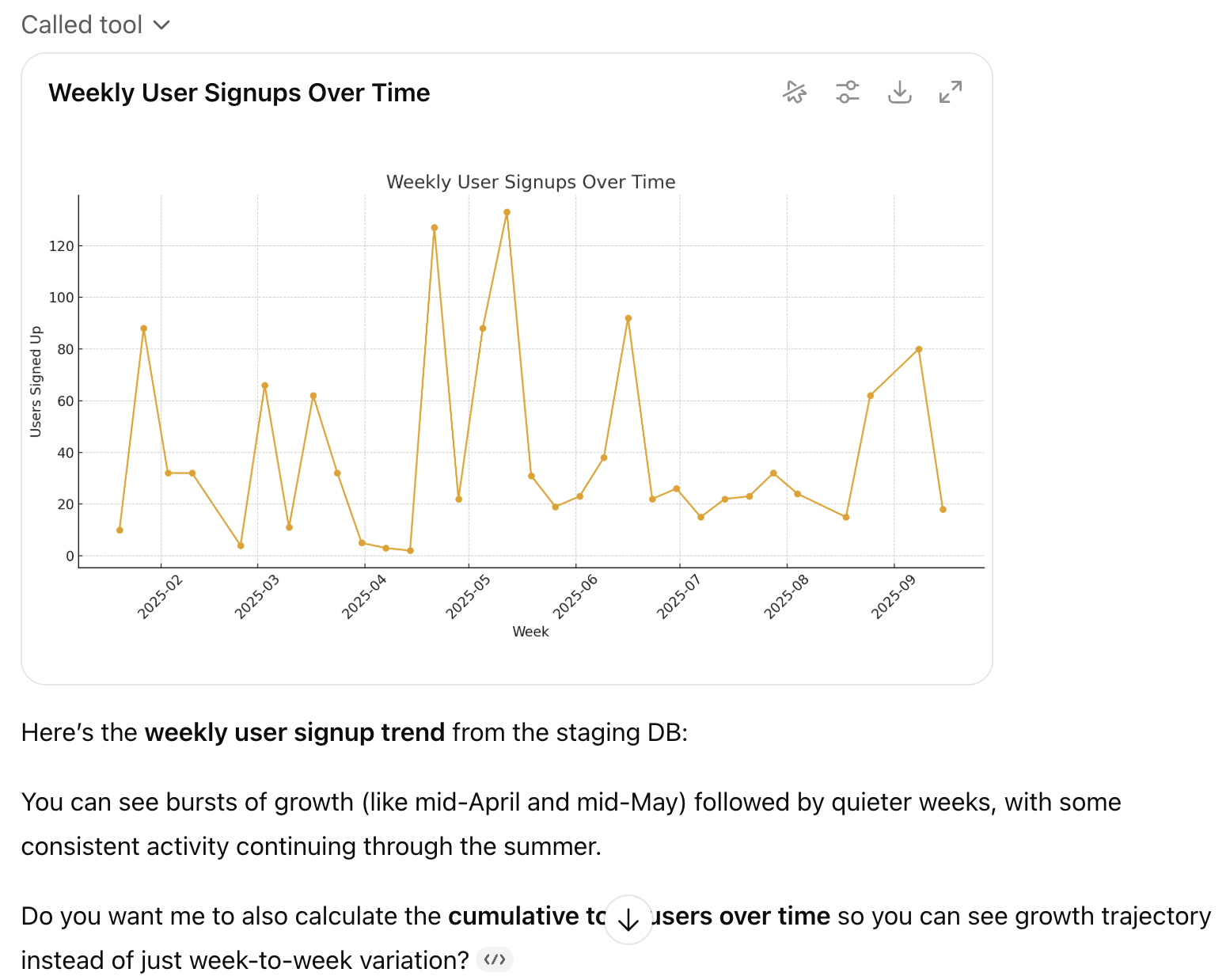
Your team uses Claude Code or Cowork to query databases in natural language. Every AI-generated query passes through your policy layer first.
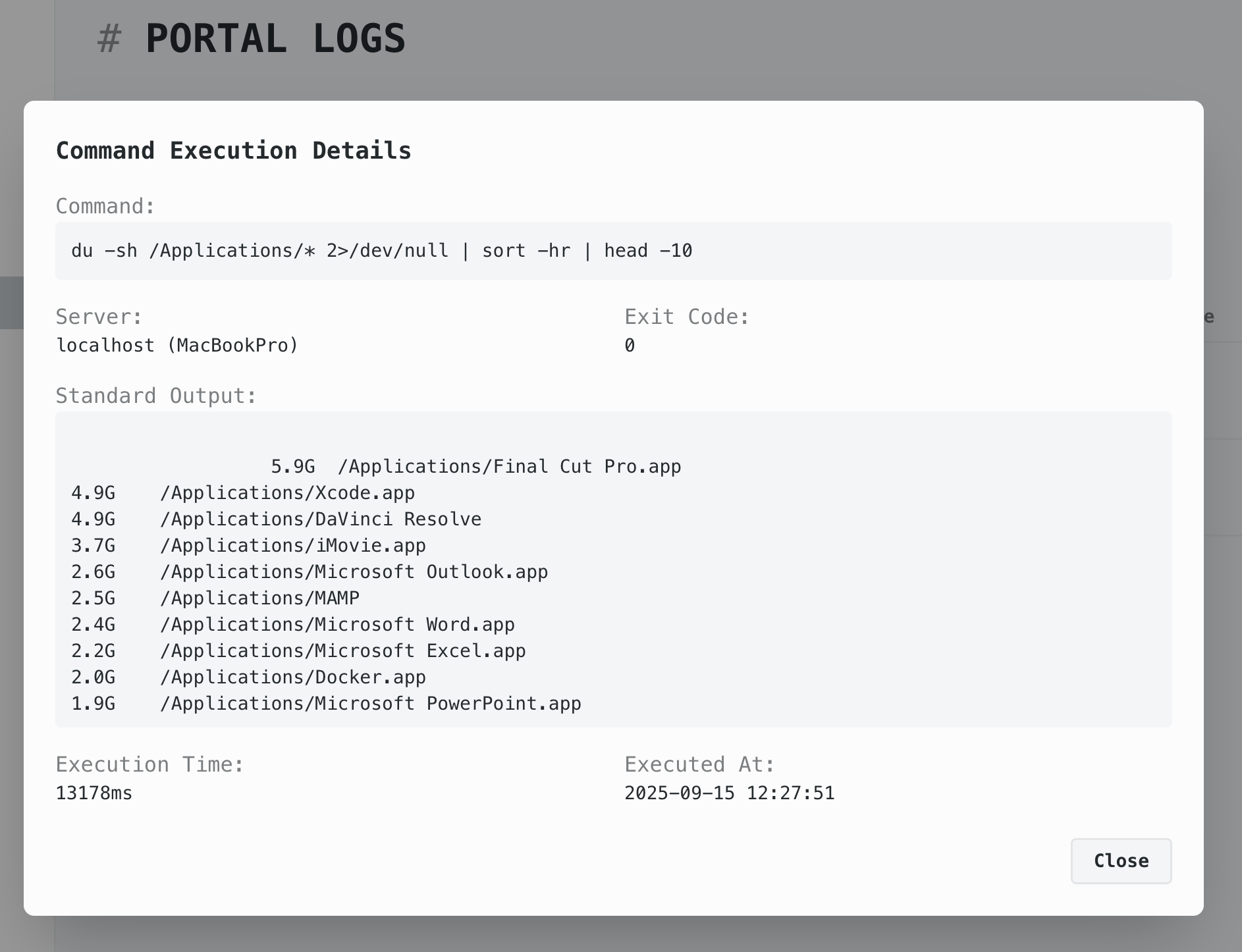
Every query, every response, every action is logged. See who asked what, when, and exactly what data was returned.
How it works
Add your databases through the Gentility dashboard. Install the lightweight open-source agent on your infrastructure. Your credentials stay in your network.
Set granular access controls: read-only defaults, query allow-lists, blocked patterns, role-based permissions. Policies are code — version them, review them, deploy them.
Connect through our MCP server. Your team queries databases using Claude Code or Cowork. Every interaction is filtered, logged, and auditable.
Privacy
Gentility is built for organizations that cannot compromise on data sovereignty. The open-source agent runs entirely within your network boundary. We provide the control plane; you keep the data plane.
The agent runs on your servers. Data never transits through our infrastructure.
We never see, store, or train on your data. Period.
All communication between components uses TLS. Credentials are encrypted at rest.
Audit every line of code that runs in your infrastructure. No black boxes.
Your infrastructure
Security
Every SQL query and shell command is parsed and validated before execution. Dangerous patterns are blocked instantly.
Complete record of every interaction: who asked, what was generated, what was executed, what was returned.
Granular permissions per user, team, and data source. Different people get different levels of access.
Write access is never assumed. Every mutation requires explicit policy authorization. Defense in depth.
Pricing
No credit card required. Upgrade as your team grows.
For individuals exploring AI-powered data access.
For teams that need governance and collaboration.
For organizations with advanced security requirements.
Set up in minutes. Works with Claude Code, Cowork, and any MCP client. Free tier, no credit card.